9 best supplier risk management solutions to safeguard your workflow
Compare key features, third-party reviews, and user ratings of supplier risk management solutions.

Relying on intuition alone to manage supplier relationships is like navigating a minefield blindfolded (risky, to say the least)!
From unexpected financial instability to potential cybersecurity breaches and unforeseen supply chain disruptions, the threats lurking in your supplier ecosystem can significantly impact your bottom line and reputation. That's why robust supplier risk management software is a strategic imperative for any forward-thinking organization.
So, how do you cut through the noise and find the solution that truly fits? We've done the heavy lifting for you. To curate this comprehensive guide, we sifted through countless third-party reviews, dissected crucial features, evaluated user ratings, and delved into the core capabilities of each platform.
Our aim is to provide you with the insights you need to confidently find the perfect partner for your risk management needs.
Best supplier risk management software at a glance
Ready to dive into the details? Here's a straightforward look at some of the top vendor risk management tools we've reviewed, listed in no particular order:
Zip
While Zip isn't a standalone supplier risk management tool that replaces specialized platforms, it can help eliminate risk management silos and enhance compliance, visibility, and efficiency throughout the entire supplier lifecycle.
Zip's agentic AI solution contains an array of AI agents purpose-built for flagging procurement risks and opportunities during supplier sourcing and selection phases. These intelligent agents also integrate seamlessly with dedicated third-party risk management (TPRM) tools (like the ones we listed below) and other platforms through Zip's central system, helping you embed risk awareness right from the start of every spend decision.
This means Zip helps your company get ahead of potential issues by bringing essential risk insights directly into your day-to-day purchasing workflows. This empowers your teams to spot and address risks proactively long before they become bigger problems.
Key features:
- Automated vendor checks: Zip helps you automatically validate things like bank accounts and tax IDs for new suppliers, which is a great way to prevent fraud right from the start.
- Smart approval workflows: Zip streamlines those tricky approval processes across different departments like procurement, legal, finance, and IT, making them easier to audit.
- Centralized supplier data: Zip creates a central hub for all your supplier data, making it easier for different teams to review contracts and potential risks together.
- Prioritize risks with scoring: The system helps you dynamically score and categorize your suppliers based on how much risk they might pose and relevant regulations, so you can focus on what matters most.
- Continuous risk monitoring: You can set up regular risk reviews to keep an eye on your suppliers over time, helping you stay ahead of new risks as they pop up.
G2 rating: 4.6 stars

Bitsight
Bitsight offers cyber risk management solutions that provide visibility into an organization's security posture and its digital supply chain. The platform translates complex cybersecurity data into security ratings, designed to help businesses communicate cyber risk and make informed decisions.
Bitsight's approach focuses on continuous monitoring and actionable insights to identify and address vulnerabilities. It gathers and analyzes vast amounts of data, which is then validated by third-party experts to accurately show how likely cyber incidents are. This helps organizations understand their cyber risk from what's visible externally, making it easier to compare their security with others and manage vendor risks on a larger scale.
Key features:
- Evidence-based security ratings: Bitsight provides objective, data-driven security ratings (250-900) for your organization and third parties, which are derived from continuous analysis of externally observable data.
- Extensive visibility: Bitsight operates one of the world's largest risk datasets, leveraging AI and technical researchers to offer unparalleled insight into attack surfaces, including shadow IT and fourth-party risks.
- Financial quantification of cyber risk: This platform translates cyber risk into financial terms, helping organizations prioritize investments, calibrate cyber insurance coverage, and communicate effectively with executives and boards.
- Validated correlation to breach: Unique in the industry, Bitsight's analytics have independent third-party validation proving their statistically significant correlation to the likelihood of cybersecurity incidents and data breaches.
G2 rating: 4.6 stars
SecurityScorecard
Similar to Bitsight, SecurityScorecard provides security ratings to objectively measure an organization's cybersecurity posture and continuously monitor hygiene for internal operations and vendors, but it distinguishes itself by using a simplified A-F grading system.
The platform assigns letter grades based on over 200 issue types, like "malware detected" or "exposed database"—with lower scores indicating a higher chance of a data breach. SecurityScorecard's method uses smart computer algorithms to predict how likely a breach is, which is then tested internally to ensure accuracy.
Key features:
- A-F security ratings: SecurityScorecard provides an easy-to-understand A-F grading system for cybersecurity posture, with a direct correlation to breach likelihood based on its proprietary scoring methodology.
- Predictive breach likelihood: Its Scoring 3.0 methodology, updated with machine learning, indicates that organizations with lower scores are significantly more likely to experience a breach compared to those with higher scores.
- Comprehensive risk factors: SecurityScorecard assesses an organization's external-facing assets across 10 key risk factors, including application security, network security, DNS health, and patching cadence.
- Collaborative remediation: The platform is designed to facilitate easy collaboration with vendors, allowing them to access their own scores and detailed findings to address issues and improve their security posture.
G2 rating: 4.3 stars
OneTrust
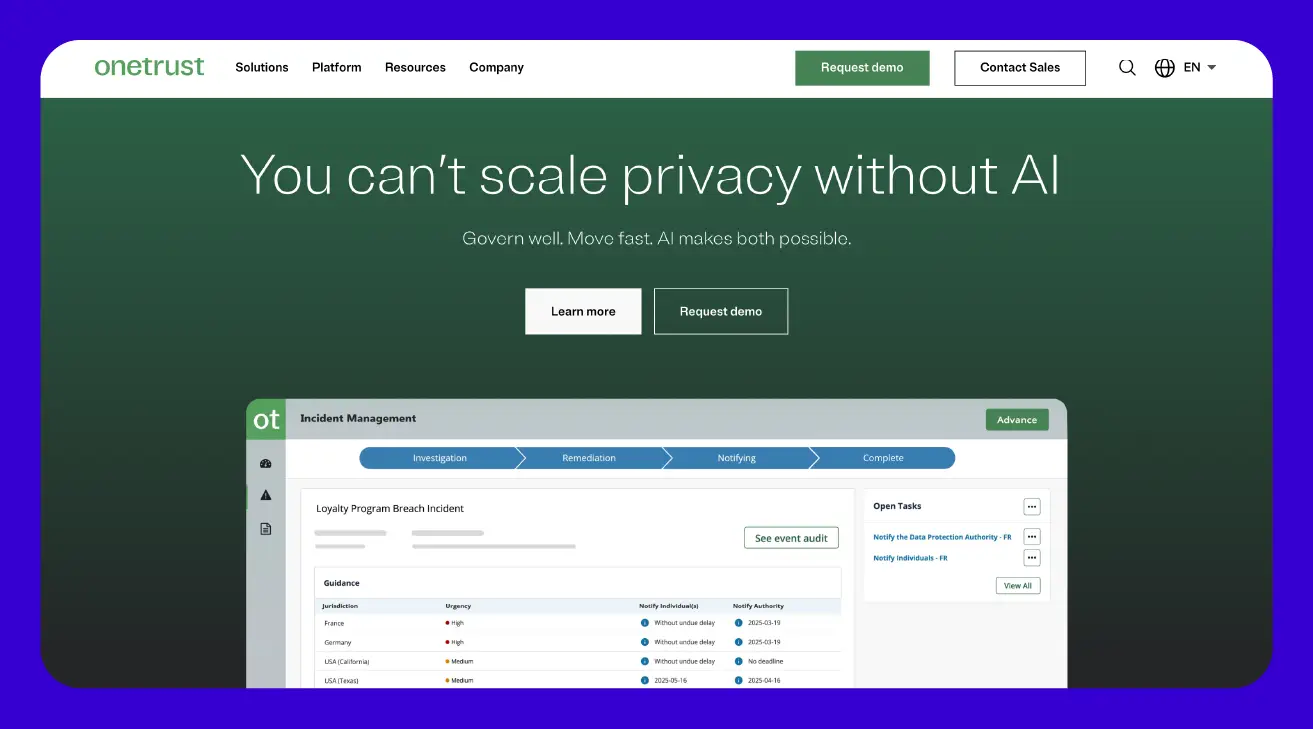
OneTrust offers a broad platform for managing risks from your third-party partners. It brings together different areas like privacy, security, IT, and even ethics into one clear approach. The platform uses smart automation to smooth out every step of working with a third party, from getting them set up and checking their risks to monitoring them over time.
Many users love how it pulls all your vendor info into one central place, giving you a clear picture of risks across your entire supply chain. However, it's worth noting that some users have found the way it looks and works can be a bit tricky to get the hang of at first, meaning you might need a little extra time to learn the ropes.
Key features:
- Integrated risk management: OneTrust offers a comprehensive platform that integrates various risk domains, including privacy, security, IT, and ethics, providing a holistic view of third-party risk.
- Automated third-party lifecycle management: The platform streamlines processes from vendor intake and onboarding to assessment, mitigation, and continuous monitoring, using configurable workflows and automation rules.
- Customizable assessments and workflows: Organizations can tailor assessment depth and triage workflows using out-of-the-box templates or by building custom assessments with conditional logic, though some users report that the initial setup can be complex.
- Scalability for enterprises: OneTrust is generally well-suited for larger enterprises with dedicated resources, but smaller organizations might find the implementation and ongoing management less ideal due to its comprehensive nature and potential pricing.
G2 rating: 4.3 stars
LogicManager
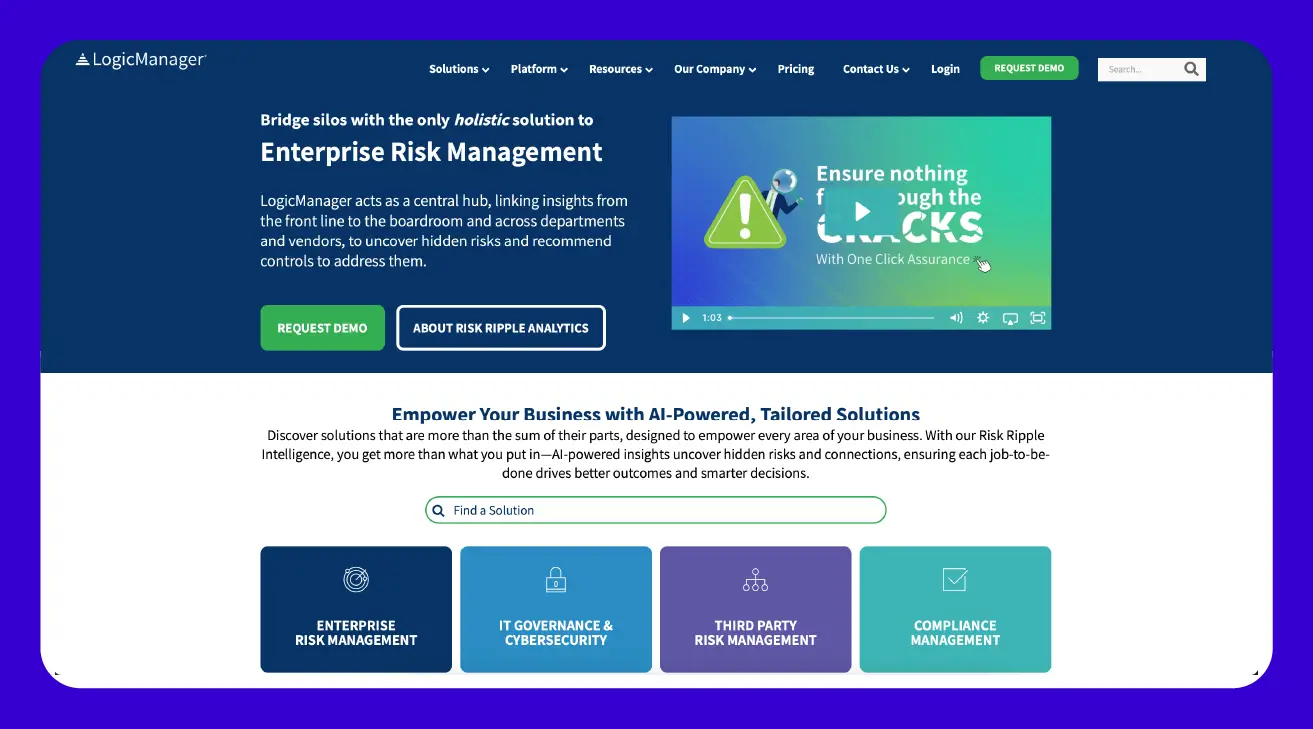
For companies looking to tie together all their risk, governance, and compliance efforts, LogicManager provides an enterprise risk management (ERM) platform that acts as a central hub. It aims to help organizations anticipate future challenges, protect their reputation, and improve performance by fostering a holistic view of risk.
Users often appreciate its ability to bring disparate risk information together and its strong customer support, with many noting that the company acts as a true partner. However, some users have mentioned that while its core features are robust, the reporting capabilities could be more flexible or intuitive, and for smaller businesses, the initial setup or overall complexity might require a bit more effort.
Key features:
- Holistic ERM approach: LogicManager connects various risk areas across the organization, including IT, finance, operations, and compliance, aiming to provide a unified view of risk rather than siloed insights.
- Reputation risk management: The platform helps organizations identify, assess, and manage risks that could impact their reputation, including those stemming from model mismanagement or operational failures.
- Risk ripple analytics: This feature uses AI-powered insights to uncover hidden risks and connections, helping organizations understand how small issues might "ripple" and affect other areas of the business.
- Outcome-based pricing model: LogicManager uses a Jobs-to-be-Done licensing model, meaning you pay for specific business outcomes achieved by the software rather than per user or for bloated features.
G2 rating: 4.5 stars
Venminder
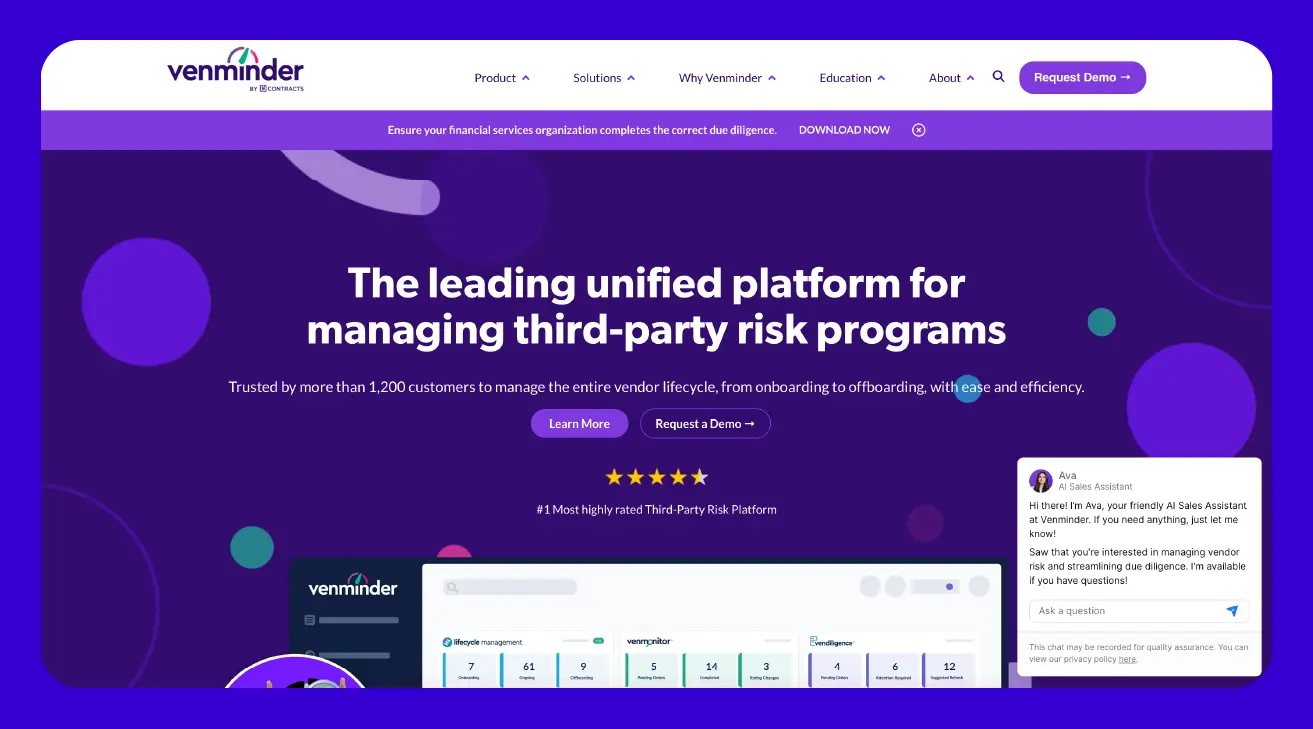
Venminder is a platform specifically designed to streamline the entire third-party risk management process. It's a one-stop solution for managing your supplier relationships, from initial onboarding and due diligence to ongoing monitoring and contract tracking.
Many users highlight Venminder's excellent customer support and the expertise of its team, which can be a huge help, especially for those new to vendor management. While the platform offers extensive features and managed services, some users have noted that the overall cost can be on the higher side, and the interface, while powerful, might feel a bit overwhelming for new users due to the sheer amount of information available. Still, for organizations needing robust support and a dedicated system for vendor risk, Venminder provides a comprehensive and expert-driven approach.
Key features:
- Managed due diligence services: Venminder stands out by offering outsourced services to collect and assess due diligence documents, including cybersecurity, business continuity, and financial health, taking a significant burden off internal teams.
- Comprehensive lifecycle management workspaces: The platform provides dedicated workspaces for each stage of the vendor lifecycle (onboarding, ongoing management, and offboarding) centralizing tasks, documents, and communications.
- Automated questionnaire management: Venminder enables organizations to build, send, manage, review, and score vendor questionnaires with customizable templates and automated workflows for increased efficiency and accuracy.
- Continuous risk intelligence (Venmonitor™): The Venmonitor™ solution provides real-time monitoring of third parties across various risk domains, like cybersecurity, business health, and financial viability, without direct supplier involvement.
G2 rating: 4.7 stars
Prevalent
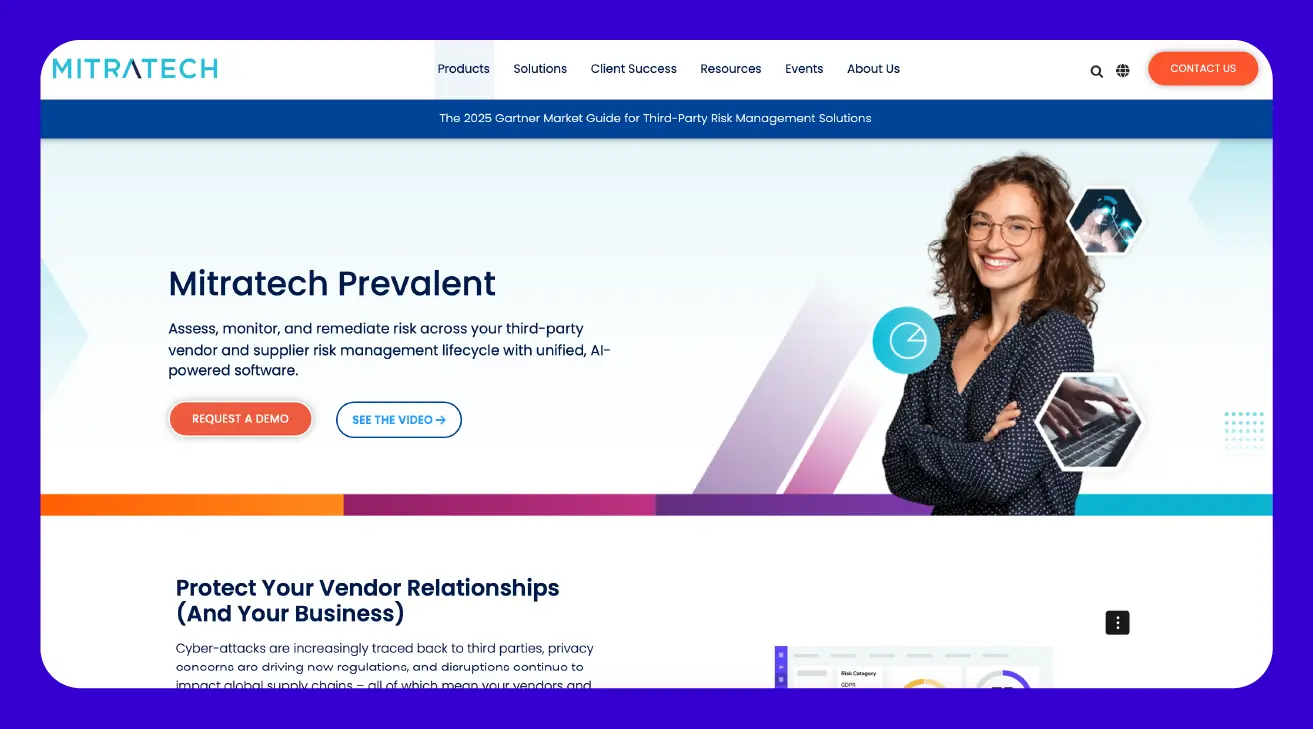
Setting itself apart from some other third-party risk management software, Prevalent offers a unified platform that focuses on automating and simplifying the entire process of supplier onboarding and assessing, managing, and monitoring risks throughout the vendor lifecycle. Users often find its system highly configurable and appreciate its strong customer support, which helps tailor the platform to specific organizational needs.
While it provides comprehensive automation for assessments and workflows, some users have pointed out that the user interface can sometimes feel a bit outdated or less intuitive, and the reporting functions might be somewhat rigid for highly customized needs. Nevertheless, Prevalent is recognized for its ability to centralize vendor risk data and streamline complex processes.
Key features:
- Unified third-party risk management platform: Prevalent provides a single, integrated platform that covers the entire third-party risk lifecycle, from vendor onboarding and assessment to continuous monitoring and remediation.
- Extensive assessment template library: The platform offers a wide range of pre-built assessment templates, including those aligned with major compliance frameworks (e.g., ISO 27001, NIST, GDPR), allowing for quick and standardized assessments.
- Third-party intelligence networks (Prevalent Exchange™): Prevalent offers access to shared intelligence networks, including data from cross-industry vendors and specialized networks (like the Legal Vendor Network), to accelerate risk checking and augment assessments.
- Managed services for TPRM: Beyond its software, Prevalent provides managed services through its Risk Operations Center (ROC), where experts can handle assessment collection and analysis, helping organizations scale their TPRM programs.
G2 rating: 4.5 stars
Black Kite
Black Kite takes a slightly different approach to vendor risk management, zeroing in on cyber intelligence to give you a fuller picture than just standard security ratings. The platform provides clear, measurable insights into cyber risks, looking not only at how technically secure a vendor is, but also at the potential financial fallout and how well they stick to rules. This helps organizations truly understand their supply chain's digital health and get ahead of problems like ransomware.
Users consistently praise Black Kite for its high-end detection capabilities, intuitive interface, and highly responsive customer support, making it a very effective and user-friendly tool for managing third-party cyber risk.
Key features:
- 3D cyber risk view: Black Kite offers a comprehensive way to look at third-party cyber risk, breaking it down from a technical angle, what it could cost financially, and how well vendors meet compliance rules. This helps you get a full picture of your exposure.
- Ransomware susceptibility index (RSI): This tool actually predicts how likely it is for a third party to get hit with a ransomware attack, giving you a heads-up so you can proactively prepare.
- Standards-based findings: All the information Black Kite gives you is tied back to well-known industry standards and frameworks (like NIST, ISO, or GDPR), so the insights aren't just smart, but also easy to act on and fit right into your existing security practices.
- AI-powered cyber assessments: Black Kite uses clever AI to look through vendor documents and its trust center data, speeding up the assessment process so you won't have to spend ages on manual questionnaires.
G2 rating: N/A
Archer
When you're dealing with risk on a large scale, especially across a huge organization with many different moving parts, Archer stands out from the crowd. Unlike some tools that might specialize in just one type of risk, Archer is built to bring all your risks, from IT and operations to compliance and third-party suppliers, into one integrated system.
This platform is designed for enterprises that need to connect all their different risk data and customize almost everything to fit their exact needs, even the really complex stuff. While it's a big investment in time and resources to get it set up, once it's humming, Archer provides a robust framework that gives large enterprises incredible control and a holistic view of their risk landscape.
Key features:
- Integrated risk management (IRM) platform: Archer provides a unified platform that connects various risk areas across the enterprise, including operational risk, IT risk, regulatory compliance, and third-party risk, giving you a holistic view.
- Highly configurable workflows and assessments: The platform offers extensive customization options, allowing you to build tailored workflows, risk assessments, and reporting dashboards to match your company's unique processes and compliance requirements.
- Centralized risk register: Archer enables you to consolidate all your risk information into a single, comprehensive risk register, making it easier to track, analyze, and report on risks across your entire organization.
- Extensive content libraries: It comes with pre-built content libraries for regulations, frameworks, and assessment templates, which can significantly accelerate your compliance and risk management efforts.
G2 rating: 4.3 stars
How to choose a supplier risk management solution
Choosing the right vendor risk management solution is important, but it doesn't have to be overwhelming. This section will walk you through the key steps to finding the perfect fit for your company. We'll help you figure out what you really need and how to evaluate the options out there.
Assess your current state
Before you start looking at new software, it’s helpful to take a good, honest look at where you stand right now. This initial assessment will help you pinpoint your company's unique challenges and define what you really need from a new system.
Here’s how:
- Identify key risks: Determine the most pressing supplier risks your company faces (e.g., financial instability, cybersecurity breaches, compliance violations, supply chain disruptions, ESG risks).
- Map current processes: Document how you currently manage supplier risk, including tools, manual efforts, and departments involved.
- Identify pain points: What are the biggest challenges or inefficiencies in your existing process? Where are the gaps in visibility or control?
- Define objectives: What do you hope to achieve with a new solution (e.g., reduce risk exposure, improve compliance, automate tasks, enhance visibility, reduce costs)?
- Involve stakeholders: Gather input from all relevant departments, including procurement, finance, legal, IT, security, operations, and sustainability, to ensure all requirements are captured.
Research potential solutions
Once you have a clear idea of your current challenges and what you need, it's time to explore what's out there. This step involves looking at different software options and seeing how they might fit your specific requirements. Don't worry, you don't have to become an expert on every single platform. Just enough to find promising candidates.
Here's where to start:
- Market scan: Begin by researching leading supplier risk management software platforms, like the ones highlighted in this article. Utilize industry reports, analyst recommendations, and online comparison sites.
- Shortlist vendors: Create a preliminary list of solutions that appear to align with your identified needs.
Create an evaluation checklist
Now that you have a shortlist of potential solutions, the next step is to build a detailed checklist for evaluation. This will help you systematically compare each option against your specific needs and priorities, ensuring you make a well-informed decision. It's like having a scorecard to make sure every important feature and capability is considered.
Here’s what to look for when creating your checklist:
- Core features: Does the software have the essential tools you need, like risk assessments, continuous monitoring, and automated workflows?
- Usability and user experience: Is it easy for everyone on your team to use, from daily users to management? Can it be customized without needing a coding expert?
- Scalability and flexibility: Can the solution grow with your company, handling more suppliers and complex needs as you expand? Can it adapt to new rules or ways your business operates?
- Vendor support and reputation: What kind of help will you get from the vendor after you buy the software? Look into their customer support, training options, and what other users say about them.
Understand pricing and ROI
Before making a final decision, it's really important to dig into the financial side of things. This means understanding not just the upfront cost, but also what kind of return on investment (ROI) you can expect. This will help ensure the solution makes good business sense in the long run.
Here's what to consider:
- Pricing model: How does the vendor charge? Is it per user, per supplier, or a tiered system? Make sure you understand all potential costs, including implementation, training, and ongoing support.
- Hidden fees: Are there any extra costs for integrations, advanced features, or additional data storage that might pop up later?
- ROI: How will this software save your company money or boost efficiency? Think about potential reductions in manual labor, averted risks (like data breaches or supply chain disruptions), and improved decision-making.
- Contract terms: What are the contract lengths, payment schedules, and renewal terms? Make sure they align with your company's financial planning.
- Budget alignment: Does the solution fit within your allocated budget, considering both initial investment and long-term operating costs?
Request demos and pilot programs
Once you've narrowed down your options, it’s time to see the software in action! Demos and pilot programs are your chance to get a hands-on feel for how each solution works in a real-world scenario. This step is crucial for validating claims and seeing if the software truly aligns with your day-to-day operations. Don't hesitate to ask specific questions about functionality, workflows, reporting, and how the vendor handles support after purchase.
Here's what to look for in the demo:
- Tailored demonstrations: Ask vendors to customize their demo to your specific use cases and pain points, showing how their solution directly addresses your challenges.
- Hands-on experience: If possible, request a trial or a proof of concept (POC) so your team can actually use the software with your own data. This is invaluable for gauging usability and fit.
- Key feature walkthroughs: Ensure the demo highlights the core features you identified in your checklist and shows how they function in practice.
- Integration capabilities: Ask to see how the software integrates with your existing systems (like ERP or accounting software) to ensure smooth data flow.
- Reference checks: If the vendor offers, speak with their current customers to get an unbiased perspective on their experience with the software and the vendor's support.
Plan for implementation and adoption
This final and equally crucial stage involves carefully planning how to bring the new software into your company and ensure everyone actually uses it effectively. A smooth rollout and good adoption are key to seeing the benefits you expect.
Here's what goes into this stage:
- Develop an implementation plan: Create a detailed roadmap outlining every step of the software deployment, including timelines, who's responsible for what, and the resources needed.
- Data migration strategy: Figure out how you'll move all your existing supplier data safely and accurately into the new system.
- Training and change management: Build a clear training program for all employees who will use the software and develop a plan to help everyone adapt to the new way of working. This can help overcome any resistance to change.
- Establish success metrics: Define how you'll measure the success of the new system after it's live. This could include things like faster onboarding times, fewer missed risks, or improved compliance rates.
- Post-implementation review: Schedule a review after the software has been in use for a while to see what's working well and what might need tweaking. This ensures continuous improvement.
Don't just manage risk, orchestrate it
With a ton of specialized supplier risk management tools out there, choosing one that covers all your company's needs can feel incredibly difficult. If you're looking for a platform that streamlines your risk management efforts across teams, tools, and data, pairing Zip with top-of-the-line TPRM solutions is your best bet.
Zip orchestrates risk from end to end, helping you manage everything from supplier onboarding to final payments. Request a demo to see how it can transform your procurement process.

Maximize the ROI of your business spend

Enter your business email to keep reading
























.webp)



















.avif)













.avif)










.webp)




.avif)












.avif)
